Silent data corruption in EHR systems occurs when patient data is altered or degraded without triggering errors, alerts, or system failures.
Healthcare teams continue using records that appear intact, backups complete successfully, and systems remain online—while the underlying clinical data is no longer reliable.
Industry recovery studies show that about 58 % of backups fail during recovery, revealing that even when backups exist, many won’t restore correctly when needed. (Source)
What is Silent Data Corruption in EHR Systems?
Silent data corruption occurs when electronic health record (EHR) data is altered, degraded, or partially damaged without triggering errors or alerts. Records remain accessible, applications function, and workflows continue—yet the data itself is no longer reliable.
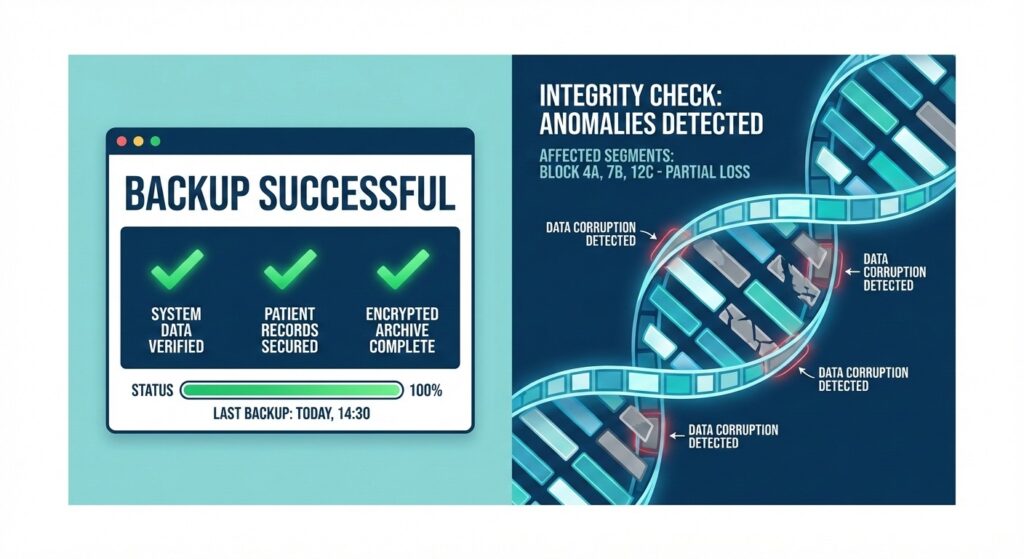
When “Backup Successful” masks underlying data decay.
Silent Data Corruption vs Data Loss and Downtime
- Data loss is visible: files are missing or inaccessible.
- Downtime is disruptive and immediately noticeable.
- Silent corruption is neither. Data exists and appears usable, but accuracy is compromised.
Why Silent Data Corruption Goes Undetected in Healthcare IT
Most healthcare environments rely on signals that confirm operations, not correctness:
- Backup jobs confirm completion, not integrity
- Checksums validate transfer, not meaning
- Monitoring focuses on uptime, not data accuracy
At scale, this matters. Large storage studies have documented hundreds of thousands of silent corruption events across millions of disks, many undetected until later scrubbing or restore attempts. Separately, industry surveys consistently show that around 50% of restore attempts fail when tested, despite backups reporting success. [source]
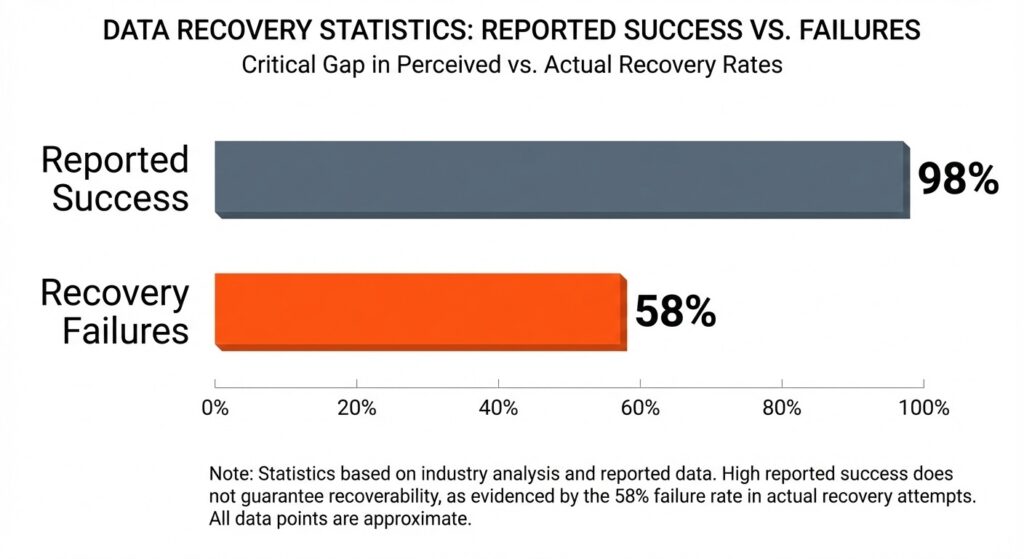
The disconnect between backup completion and recovery reality.
How Corrupted EHR Data Remains Usable but Inaccurate
Silent corruption often manifests as:
- Partially degraded patient records
- Incorrect or mismatched metadata
- Broken relationships between datasets
Because EHRs are interconnected with labs, imaging, and billing systems, even small integrity faults can ripple across clinical workflows without obvious failure.
Why Are EHR Systems Vulnerable to Silent Data Corruption?
EHR platforms combine several structural traits that increase exposure to undetected corruption.
High-Frequency Clinical Data Writes in EHR Workflows
EHRs are continuously updated by:
- Clinician documentation
- Device and monitor integrations
- Lab and imaging feeds
- Revenue cycle and coding systems
High write volume increases the likelihood that small integrity errors occur without interrupting operations.
Long-Term Retention of Patient and Medical Records
Healthcare data is retained for years—often decades. Over time:
- Storage media degrades
- Systems change
- Data is migrated and re-backed up repeatedly
The longer data lives, the more opportunities exist for silent degradation.
Interdependencies Between EHR, Imaging, Lab, and Billing Systems
EHRs do not operate in isolation. Corruption affecting identifiers, timestamps, or indexes may not break any single system—but it can quietly desynchronize many of them.
Common Causes of Silent Data Corruption in Healthcare Environments
Silent corruption typically results from normal operations interacting with complex infrastructure.
Storage Degradation and Bit-Level Data Errors
All storage media ages. Bit flips and sector degradation may be silently corrected—until correction fails. Large-scale analyses show hundreds of thousands of silent corruption events, many not detected at the time data was written.
Snapshot, Replication, and Synchronization Inconsistencies
EHR environments depend on:
- Snapshots
- Replication
- System synchronization
When these processes capture data mid-change, backups may complete successfully while preserving inconsistency.
Backup Processes That Replicate Already Corrupted Data
Backups preserve state, not truth. If data is corrupted before backup:
- Every successful backup reinforces the problem
- Incremental propagate it forward
- Retention policies preserve it for years
This helps explain why a majority of recoveries can still fail, even when backup jobs report success, as shown in studies where 58% of recoveries do not succeed. [source]
Malware and Ransomware That Alter Data Without Encryption
Not all attacks encrypt data. Some malware subtly alters records or metadata, allowing corrupted data to persist across backups without triggering alarms.
Why Backup Systems Rarely Detect Silent Data Corruption?
Backup platforms are designed to validate process completion—not data usability.
What “Backup Successful” Actually Validates
A successful backup means:
- The job ran
- Data transferred
- No transport errors occurred
It does not confirm:
- Logical consistency
- Application usability
- Clinical accuracy
Limits of Checksums and Transfer Validation
Checksums verify that data arrived unchanged during transfer. They cannot detect:
- Pre-existing corruption
- Broken relationships across records
- Application-level inconsistencies common in EHRs
How Silent Data Corruption Propagates Through Backup Chains
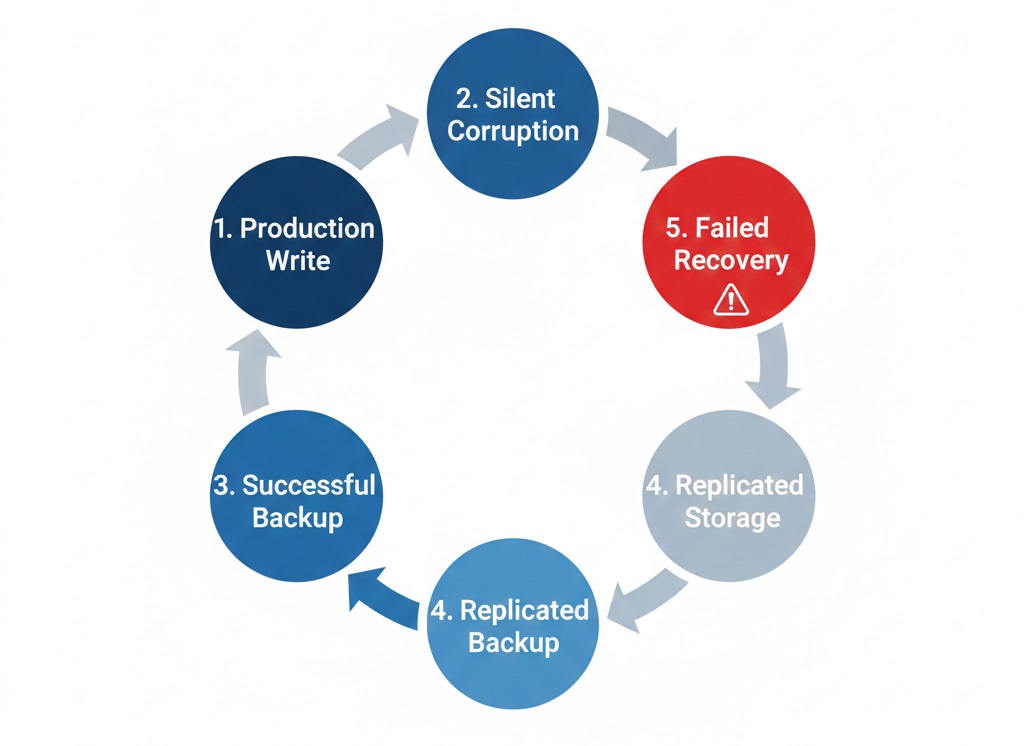
How silent corruption spreads through your backup infrastructure over time.
Once corruption enters the backup environment:
- Incremental compound it
- Replication spreads it
- Long retention preserves it
Because only a small percentage of organizations test restores daily, silent corruption often remains hidden until recovery becomes unavoidable.
How Healthcare Organizations Discover Silent Data Corruption?
Discovery rarely comes from monitoring. It comes from forced validation.
Restore Failures During Disaster Recovery Events
During recovery, organizations may find:
- EHR databases fail validation
- Records restore but cannot be reconciled
- Applications load but behave inconsistently
This aligns with findings that around 50% of restore attempts fail when tested.
Data Integrity Issues Uncovered During HIPAA Audits
Audits often surface:
- Incomplete patient histories
- Inconsistent timestamps or logs
- Gaps between production systems and backups
Because integrity is a HIPAA requirement, inability to prove restore accuracy creates immediate compliance exposure.
Silent Data Corruption Exposed During EHR Migrations
Migrations force reindexing and validation. They frequently reveal:
- Corrupted historical data
- Broken data relationships
- Incomplete longitudinal records
Industry surveys indicate that only about one‑third of organizations achieve full recovery of all data after a major incident, meaning the rest experience partial or failed recovery, often tied to data integrity or recovery‑process issues. [sources]
Why Silent Data Corruption Creates Compliance and Patient Safety Risk
Silent corruption transforms integrity into a regulatory and clinical issue.
HIPAA Data Integrity and Availability Requirements
The HIPAA Security Rule requires covered entities to implement safeguards to ensure the integrity and availability of ePHI, including electronic mechanisms to corroborate that ePHI has not been altered or destroyed in an unauthorized manner [source]
Audit Risk When Restore Accuracy Cannot Be Proven
Auditors increasingly expect evidence that data can be restored and validated. Because Only about 15% of organizations test their backups daily, and another 25% test weekly, which means many providers lack recent, systematic proof that their backups will restore correctly when needed [source]
Clinical Impact of Inaccurate or Incomplete Patient Records
Silent corruption can distort:
- Medication histories
- Lab associations
- Imaging references
Because systems remain operational, these inaccuracies may influence care before detection—creating direct patient safety risk.
How Healthcare Organizations Can Detect Silent Data Corruption
Detection requires validating outcomes, not monitoring activity.
Why Restore-Based Verification Matters More Than Backup Monitoring
Monitoring confirms jobs ran. Verification confirms restored EHR data works. Detection improves when organizations:
- Restore data into isolated environments
- Validate record completeness
- Test clinical workflows on restored systems
The Role of Periodic Restore Testing in EHR Environments
Effective detection includes:
- Full and partial EHR restores
- Historical data validation
- Cross-system dependency checks
Without restore testing, silent corruption can persist indefinitely.
Using Recovery Validation to Confirm EHR Data Integrity
Recovery validation produces:
- Documented restore outcomes
- Integrity evidence suitable for audits
- Early detection of long-standing corruption
Why Backup Verification Matters More Than Backup Completion
Backup completion proves a process ran. Verification proves data is safe to use. Without backup verification and recovery, healthcare organizations cannot confidently restore accurate, complete EHR data when it matters most.
Backup Monitoring vs Recovery Validation
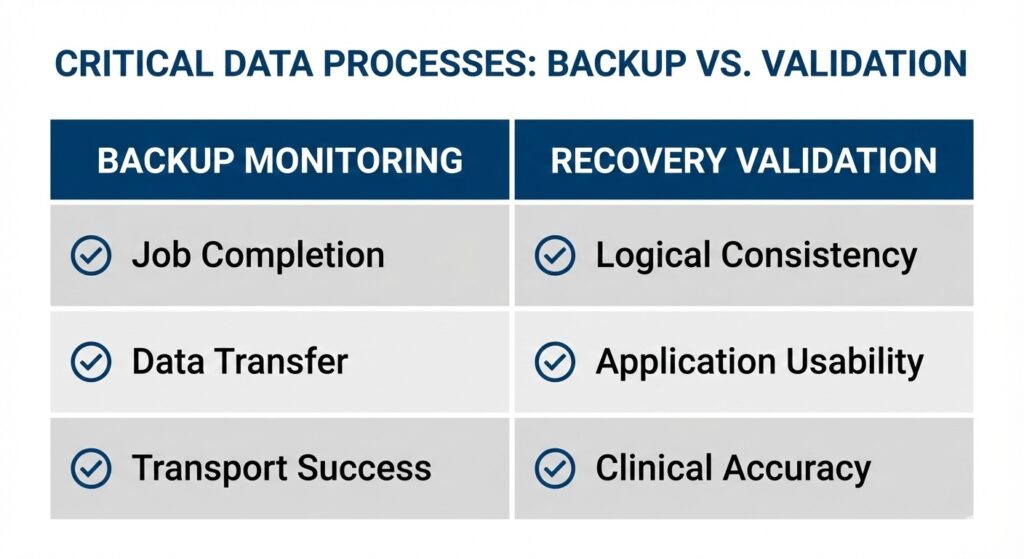
Moving from “Did it run?” to “Does it work?”
- Monitoring asks: Did it run?
- Validation asks: Does it work?
Given that roughly half of restore attempts fail when tested, completion alone is not evidence of recoverability.
How verified recovery prevents corrupted EHR restores
Verified recovery ensures:
- Restore points are tested before emergencies
- Integrity issues are identified early
- Corrupted data is not reintroduced into production
When healthcare organizations should validate backups
Validation is critical:
- After EHR upgrades or schema changes
- After storage or replication changes
- After suspected malware activity
- On a recurring schedule aligned with clinical risk
If a restore would be required to maintain patient care, it should be validated before an incident forces it.
Final Takeaway: Silent Data Corruption Is a Recovery Risk, Not a Backup Metric
Silent data corruption is not a backup failure you see—it’s a recovery failure you discover too late. Healthcare organizations that rely on backup completion alone cannot prove data integrity, compliance readiness, or recovery reliability.
FAQS About Silent Data Corruption in EHR Systems
Can Silent Data Corruption Spread Across Hybrid or Cloud EHR Environments?
Silent data corruption spreads across hybrid and cloud EHR environments when replication copies corrupted records between on-prem and cloud systems, allowing integrity issues to persist across platforms without detection.
Does Immutable Backup Storage Prevent Silent Data Corruption in Healthcare?
Immutable backup storage prevents deletion and encryption but does not prevent silent data corruption, because immutable systems preserve corrupted EHR data exactly as it existed at the time of backup.
How Does Silent Data Corruption Affect EHR Recovery Time Objectives?
Silent data corruption impacts recovery objectives by causing restore delays, validation failures, and unusable EHR data, increasing recovery time objectives even when backup systems meet uptime targets.
Can Silent Data Corruption Impact Cyber Insurance or Breach Response Claims?
Silent data corruption affects cyber insurance claims when organizations cannot prove data integrity or successful restoration, weakening evidence required for breach response, recovery reimbursement, and compliance validation.
What Is the Difference Between Data Integrity Monitoring and Recovery Integrity Validation?
Data integrity monitoring tracks system health indicators, while recovery integrity validation confirms restored EHR data accuracy and usability, ensuring patient records function correctly after backup restoration.



