Why “Backup Successful” Does Not Mean Healthcare Systems Can Recover?
“Backup successful” in healthcare only means data was copied without error.
It does not prove that systems can be restored, clinical applications will function, or patient care can safely resume during an incident.
Healthcare backups often succeed while:
- Data is already compromised
- Restores fail at runtime
- Clinical systems cannot operate after recovery
- Compliance requirements for availability and integrity are unmet
Backup success confirms process completion, not recovery readiness.
Why the “Backup Successful” Message Is Misleading in Healthcare?
Healthcare environments rely on complex, stateful systems where recovery failure impacts:
- Patient access to records
- Diagnostic and treatment timelines
- Regulatory and audit exposure
Because backups are designed to report job status—not restore outcomes—organizations can appear protected while remaining operationally vulnerable.
To understand why this assumption persists, it’s necessary to separate what “backup successful” actually confirms from what it never validates in healthcare systems.

Backup success is a signal; verified recovery is the proof required for patient care.
What Does “Backup Successful” Actually Confirm in Healthcare IT?
A healthcare system reporting “Backup Successful” confirms one outcome only:
The backup process completed without detecting a fatal error.
This signal reflects process execution, not recovery capability.
What “Backup Successful” confirms
- The backup job ran to completion
- No blocking errors were detected
- Data was written to a storage target
What “Backup Successful” does not confirm
- That data can be restored into a working system
- That applications will function after restore
- That records are complete or usable
- That the restore point is safe
- That recovery would withstand audit scrutiny
A backup can succeed even when recovery will fail.
Why Backup Success and Recovery Readiness Are Not the Same?
Healthcare systems rely on:
- Stateful EHR databases
- Continuous transactions
- Interdependent clinical applications
Backup software does not validate system reassembly or usability, so partial or inconsistent states are captured without error.
Backup Status Reports Jobs, Not Recovery Outcomes
| Backup Confirms | Recovery Requires |
| Job completion | Restore execution |
| Error-free run | Application functionality |
| Data stored | Usable, safe systems |
Backup tools report on jobs.
Healthcare depends on outcomes.
If backup success does not guarantee recovery, the next question is why restores fail so often in healthcare environments.
Why Healthcare Backups Commonly Fail During Restore?
Healthcare backup failures occur during restore, not during backup.
Restore introduces conditions that backups never test:
- System rebuild order
- Transaction reconciliation
- Application dependency alignment
Backups capture data.
Restores must reconstruct working clinical systems.
Why Stateful Healthcare Systems Increase Restore Failure Risk?
Restore risk increases due to:
- Stateful EHR architectures
- Always-active workloads
- Tightly coupled clinical systems
- Large, sequential restore requirements
A restore can complete while systems remain unusable.
Common Post-Restore Clinical System Failures
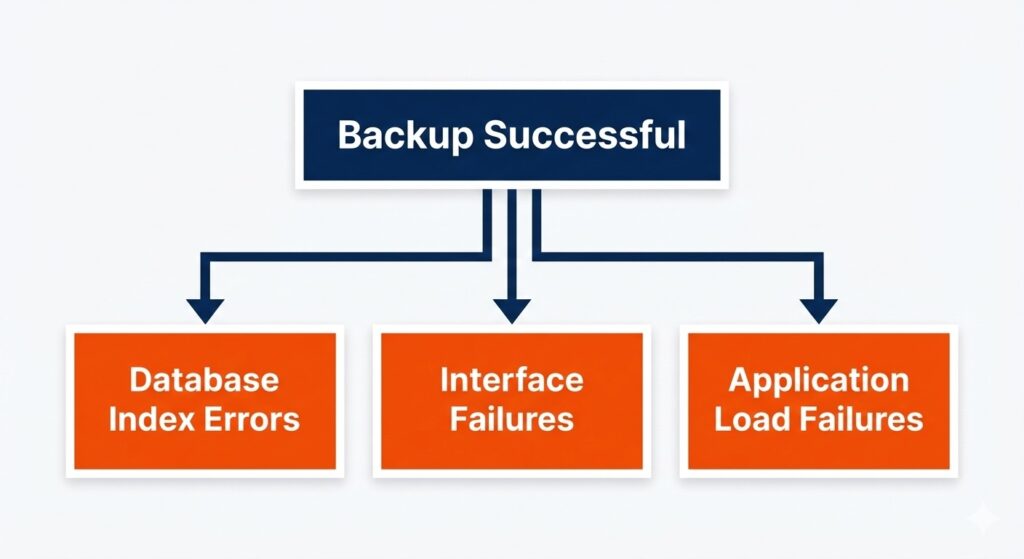
Restore failures are runtime problems that remain invisible in backup logs.
- Applications launch but fail under load
- EHRs open but records fail to load
- Databases restore with inconsistent indexes
- Interfaces between systems fail
These issues surface only during recovery, not in backup logs.
Key takeaway
- Backup success is necessary, but never sufficient.
Restore failure is a runtime problem, not a backup problem.
Restore failure becomes more dangerous when the backup itself is unsafe — which is exactly how ransomware exploits backup environments.
How Does Ransomware Compromise Healthcare Backups Before Detection?
Modern ransomware does not act immediately. It waits.
Ransomware exploits the gap between data being backed up and data being safe.
Typical behavior of ransomware includes:
- Quiet persistence
- Observation of backup schedules
- Gradual data manipulation
- Delayed encryption
During this period, backups continue to report success.
Why Backup Systems Fail to Detect Compromised Restore Points?
Backup systems cannot detect:
- Malicious changes that resemble normal updates
- Embedded malware within datasets
As a result, multiple restore points can become unsafe without alerts.
Why the Most Recent Backup Is Often the Most Dangerous
During incidents, teams often restore the most recent backup — which is frequently the most compromised.
This leads to:
- Reinfection after recovery
- Restarted outages
- Extended downtime
Key takeaway :
- Ransomware exploits the gap between data being backed up and data being safe to restore.
- Even without ransomware, healthcare organizations still face scrutiny over whether backup success proves recoverability.
Why Does Backup Success Not Prove HIPAA-Compliant Recoverability?
HIPAA requires availability and integrity of ePHI — not the existence of backups.
Backup success does not prove either.
What Healthcare Auditors Require as Recovery Evidence
Audits focus on:
- Whether systems can be restored
- Whether data is usable
- Whether recovery can be demonstrated
Backup logs do not answer these questions.
The Compliance Gap Between Backup Logs and Recovery Proof

Auditors require proof of usability, not just evidence of a backup job.
This gap typically appears after an incident, when evidence is demanded.
Key takeaway :
From a compliance perspective, backup success is supporting information, not proof. This gap between assumption and proof is why healthcare recovery standards are shifting.
What is Verified Recovery and Why Is It Required in Healthcare?
Verified recovery exists to answer one question:
Can systems be restored safely and support patient care right now?
Verified Recovery Proves Systems Can Support Patient Care
At a conceptual level:
- Recoverability is demonstrated, not assumed
- Restore points are known to be usable
- Evidence exists before incidents occur
This replaces hope with proof.
Backup Success vs Verified Recovery: Signal vs Proof
| Backup Success | Verified Recovery |
| Confirms data was copied | Confirms systems can be restored |
| Measures job completion | Measures recovery outcomes |
| Relies on logs | Relies on evidence |
Backup success is a signal.
Verified recovery is assurance.
This is why healthcare organizations are moving toward backup verification and recovery as a distinct standard.
Final Takeaway: Backup Success Indicates Progress, Not Safety
A “backup successful” message indicates progress — not safety.
In healthcare, only verified recovery closes the gap between data existence and care continuity.
Backup Successful in Healthcare FAQs
How often should healthcare organizations test disaster recovery plans?
Healthcare organizations should test disaster recovery plans at least once every 6–12 months to validate system availability, recovery timelines, and patient care continuity under real incident conditions.
What is the difference between backup retention and recovery readiness?
Backup retention stores data for a defined period, while recovery readiness confirms systems can be restored and function correctly within required downtime limits for clinical operations.
Can cloud backups alone ensure healthcare data recoverability?
Cloud backups alone do not ensure recoverability. Healthcare recovery depends on validated restores, application integrity, and documented recovery outcomes—not storage location.
What role does RTO and RPO play in healthcare recovery planning?
RTO defines how quickly systems must be restored, and RPO defines acceptable data loss. Healthcare recovery planning aligns backups and restores to meet both clinical and regulatory thresholds.
Who is responsible for recovery verification in healthcare organizations?
Healthcare recovery verification is a shared responsibility between IT, compliance, and clinical operations to ensure restored systems support patient care and meet audit requirements.
Last updated on February 4, 2026



